Chain mail
It’s highly unlikely that chain mail contains relevant information. If you forward it, you’re just wasting everyone’s time.
Hundreds of high-quality videos that are relatable and retainable — with a dash of humor


Original and high-quality content — from interactive videos to digital nudges
High-quality videos based on real-life scenarios with a dash of humor but no cartoons
Quizzes, posters, stickers and checklists for your internal communication to keep cybersecurity top-of-mind
White papers, learning tools and stakeholder analyses to learn from, get stakeholders buy-in or just share within the company
AwareGO’s content is incredibly pointed. Videos make employees see their work environment through real-world examples.

It’s highly unlikely that chain mail contains relevant information. If you forward it, you’re just wasting everyone’s time.



8 million people are each day opening phishing e-mails, and this is the source of most cyberattacks.


Make your IT technician’s job easier and don’t install software on your work computer without permission.

One of the most valuable cybersecurity knowledge to have is how to spot phishing emails easily and avoid giving away private password and credentials.
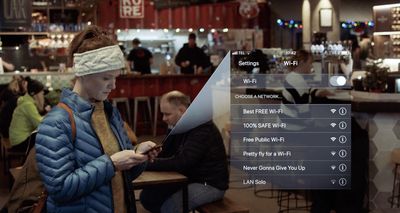
Hackers can set up a WiFi access point, and if you connect to it, much of your communication can be monitored or even manipulated.

A VPN connection creates a virtual tunnel between your laptop or smart device and your office servers.
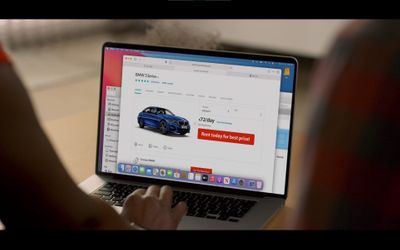
The biggest risk when shopping online is not that you could simply lose your money.

Make sure that only employees have access to the workplace, both during and outside working hours.

“Insider threat” usually refers to employees who leak data, but data can also leak out because of their friends.

Keep your computer safe and locked when working from home.

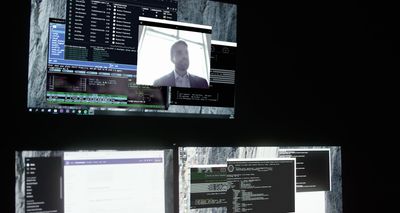
When it comes to distributing viruses, spyware, or other malware, there is no method more popular among hackers than attachments.

If you install unapproved software on your work computer, the whole office network could become infected with a virus.

All workplaces should have strong policies and procedures in place when it comes to letting strangers into restricted areas.


Be aware that there is always a possibility that someone has been “listening in” on your email conversations.
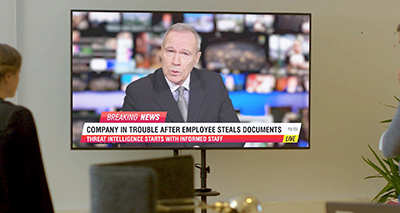
Sometimes security breaches are performed by employees, willingly or accidentally.

Creating and maintaining a good security culture in the workplace is something that all businesses should strive for.


Accepting software updates or downloads from a website is risky business.

Do not enable editing on Office documents unless you’re absolutely sure.


It’s easier to steal physical data than hacking into databases or guessing passwords.

A tone of urgency in an email is one of the key indicators of a phishing email.


Can your clients trust you with their information? Do you guard it like it is your own?

When we know about the dangers all around us, we can take precautions and try to navigate our world more safely.




Patching your software whenever you get notified of an available update could save you a lot of trouble and time in the long run.

Hackers have been after passwords since the dawn of the Internet and they are surprisingly adept at stealing them and even guessing them.

If you are trusted with confidential information on electronic media or printouts, leaving them in an unsupervised car is not safe.

Fraudsters might try to sneak a bogus invoice into your accounting department. You should always double-check new account numbers.

The main risk factor when using a networked printer is that if you select the wrong printer, confidential material can reach unauthorized eyes, inside or outside the workplace.

Sometimes confidential information leaks out because email senders are in a hurry or distracted and select the wrong recipient.

Beware! Malware could be installed on your smartphone that turns on your camera and microphone to listen in on your conversations.

Be extra careful about who you deliver confidential information to, and make sure the recipient has the authority to access it.

Read up on the privacy laws you need to follow in your day-to-day work. Failure to comply might result in fines for your workplace.

Hover over links in emails before you click on them to make sure they’ll lead you to the right place.

Think twice before you post or comment on your social media sites. How will this reflect on you or your workplace?

Using a privacy screen, or privacy filter, is an affordable way to increase your security when working outside the office.

Leaving your computer unlocked and unattended can cause serious problems if someone else has access to it.

Managing multiple passwords can be hard, but here’s why you shouldn’t use the same password for every account.

When a person calls you on the phone and uses a false reason or claim to trick you into handing over personal or sensitive information, such as your social security number or credit card information, that’s called Vishing.

Documents, memos, emails, and contacts can be stolen if you leave your phone unlocked.

You can infect your computer with ransomware by various means, like opening an attachment or updating your computer from an untrustworthy source. It can be very expensive to recover your files.

A data leak is the intentional or unintentional release of secure or private/confidential information to an untrusted environment.


Always double-check unusual requests from your boss, especially regarding financial transfers.

A lot of valuable information could be gathered by going through your workplace’s trash.

Don’t share confidential information with people who do not have authorisation. Not even your best friends.

If you’re working from home, make sure your home WiFi is secure and encrypted.

What should you do when you find a USB flash drive? Whatever you do, don’t plug it into your computer.

Cyber criminals don’t just guess or hack your password. Sometimes they simply watch you type it in.

Your personal email and online storage are usually not a safe as your work email.
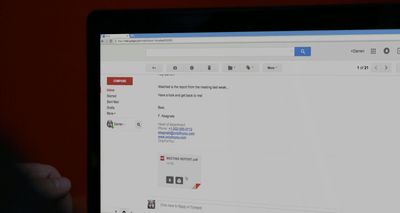

All mail is not necessarily good mail. Don’t open attachments or links from unknown senders.


It’s easy for hackers to monitor what other people are doing when they’re connected to the same free WiFi.

It’s hard to juggle multiple passwords, but writing them down and storing them by your computer is what hackers are hoping for.

There is a risk to using removable media. Make sure to encrypt your documents in case your flash drive gets lost or stolen.

To create a strong password, it’s best to use a combination of lower case and upper case letters, symbols, and numbers.


Inter-office emails can be fun, but we still need to remember proper email etiquette.

Hackers rely on the kindness of strangers to gain access to restricted areas.

A website address starting with HTTPS is encrypted and much safer than a website address starting with HTTP.

Knowing about someone’s interests and hobbies is valuable and helps hackers create spear phishing emails specifically designed for that person.

It’s highly unlikely that chain mail contains relevant information. If you forward it, you’re just wasting everyone’s time.



8 million people are each day opening phishing e-mails, and this is the source of most cyberattacks.


Make your IT technician’s job easier and don’t install software on your work computer without permission.

One of the most valuable cybersecurity knowledge to have is how to spot phishing emails easily and avoid giving away private password and credentials.

Hackers can set up a WiFi access point, and if you connect to it, much of your communication can be monitored or even manipulated.

A VPN connection creates a virtual tunnel between your laptop or smart device and your office servers.


The biggest risk when shopping online is not that you could simply lose your money.

Make sure that only employees have access to the workplace, both during and outside working hours.

“Insider threat” usually refers to employees who leak data, but data can also leak out because of their friends.

Keep your computer safe and locked when working from home.


When it comes to distributing viruses, spyware, or other malware, there is no method more popular among hackers than attachments.

If you install unapproved software on your work computer, the whole office network could become infected with a virus.

All workplaces should have strong policies and procedures in place when it comes to letting strangers into restricted areas.


Be aware that there is always a possibility that someone has been “listening in” on your email conversations.

Sometimes security breaches are performed by employees, willingly or accidentally.

Creating and maintaining a good security culture in the workplace is something that all businesses should strive for.


Accepting software updates or downloads from a website is risky business.

Do not enable editing on Office documents unless you’re absolutely sure.


It’s easier to steal physical data than hacking into databases or guessing passwords.

A tone of urgency in an email is one of the key indicators of a phishing email.


Can your clients trust you with their information? Do you guard it like it is your own?

When we know about the dangers all around us, we can take precautions and try to navigate our world more safely.




Patching your software whenever you get notified of an available update could save you a lot of trouble and time in the long run.

Hackers have been after passwords since the dawn of the Internet and they are surprisingly adept at stealing them and even guessing them.

If you are trusted with confidential information on electronic media or printouts, leaving them in an unsupervised car is not safe.

Fraudsters might try to sneak a bogus invoice into your accounting department. You should always double-check new account numbers.

The main risk factor when using a networked printer is that if you select the wrong printer, confidential material can reach unauthorized eyes, inside or outside the workplace.

Sometimes confidential information leaks out because email senders are in a hurry or distracted and select the wrong recipient.

Beware! Malware could be installed on your smartphone that turns on your camera and microphone to listen in on your conversations.

Be extra careful about who you deliver confidential information to, and make sure the recipient has the authority to access it.

Read up on the privacy laws you need to follow in your day-to-day work. Failure to comply might result in fines for your workplace.

Hover over links in emails before you click on them to make sure they’ll lead you to the right place.

Think twice before you post or comment on your social media sites. How will this reflect on you or your workplace?

Using a privacy screen, or privacy filter, is an affordable way to increase your security when working outside the office.

Leaving your computer unlocked and unattended can cause serious problems if someone else has access to it.

Managing multiple passwords can be hard, but here’s why you shouldn’t use the same password for every account.

When a person calls you on the phone and uses a false reason or claim to trick you into handing over personal or sensitive information, such as your social security number or credit card information, that’s called Vishing.

Documents, memos, emails, and contacts can be stolen if you leave your phone unlocked.

You can infect your computer with ransomware by various means, like opening an attachment or updating your computer from an untrustworthy source. It can be very expensive to recover your files.

A data leak is the intentional or unintentional release of secure or private/confidential information to an untrusted environment.


Always double-check unusual requests from your boss, especially regarding financial transfers.

A lot of valuable information could be gathered by going through your workplace’s trash.

Don’t share confidential information with people who do not have authorisation. Not even your best friends.

If you’re working from home, make sure your home WiFi is secure and encrypted.

What should you do when you find a USB flash drive? Whatever you do, don’t plug it into your computer.

Cyber criminals don’t just guess or hack your password. Sometimes they simply watch you type it in.

Your personal email and online storage are usually not a safe as your work email.


All mail is not necessarily good mail. Don’t open attachments or links from unknown senders.


It’s easy for hackers to monitor what other people are doing when they’re connected to the same free WiFi.

It’s hard to juggle multiple passwords, but writing them down and storing them by your computer is what hackers are hoping for.

There is a risk to using removable media. Make sure to encrypt your documents in case your flash drive gets lost or stolen.

To create a strong password, it’s best to use a combination of lower case and upper case letters, symbols, and numbers.


Inter-office emails can be fun, but we still need to remember proper email etiquette.

Hackers rely on the kindness of strangers to gain access to restricted areas.

A website address starting with HTTPS is encrypted and much safer than a website address starting with HTTP.

Knowing about someone’s interests and hobbies is valuable and helps hackers create spear phishing emails specifically designed for that person.
Crafted in a combined effort by film-makers, behavioral and cybersecurity experts
If people doze off during the training, they aren’t learning. AwareGO videos are fun, engaging and highly relatable
Relatable content makes it easy for the employees to apply learnings in their daily work
Compliance is easy if the training is fun, engaging and short — so it doesn’t hurt employee productivity
Increase engagement and awareness with digital nudges
Every video lesson comes with a 1-question quiz to reinforce the learning moment.
Our “good habit” posters, stickers and newsletters can be shared through digital communication channels. But also printed out and placed in offices.
Slice and dice the content from our reinforcement materials so it fits your cybersecurity plans and tone of voice.
When you need help with stakeholders buy-in
160 cybersecurity leaders in our panel share their opinions, techniques and experiences with us. Learn from them
Our introductory content helps you build the case for stakeholders what we need security awareness
Product and methodology overviews that give insights into our approach to cybsersecurity awareness
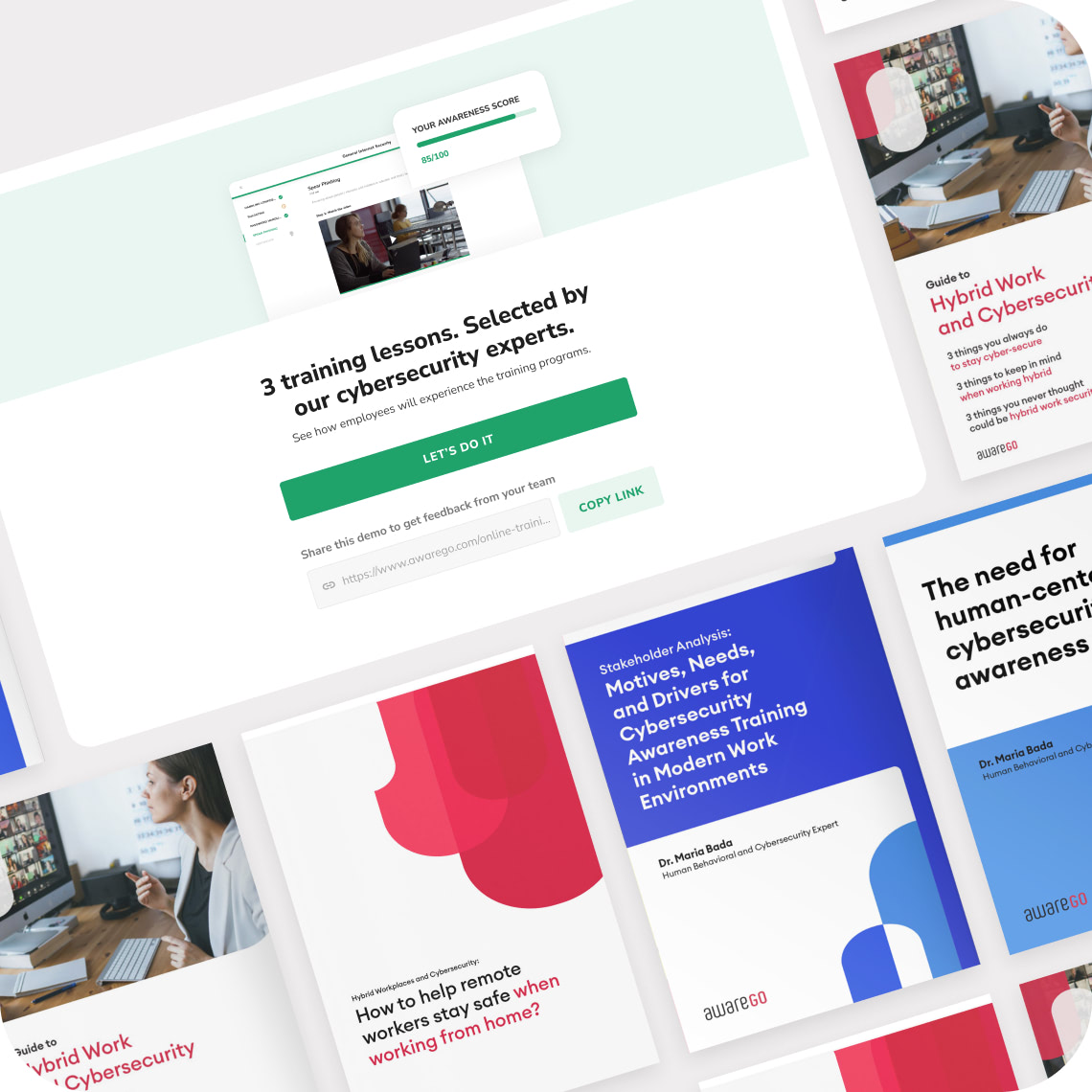
Deliver through our cloud platform or SCORM
If you already have an existing delivery solution in place, easily integrate our content with code snippets or the SCORM 1.2 and SCORM 2004 3rd edition standards
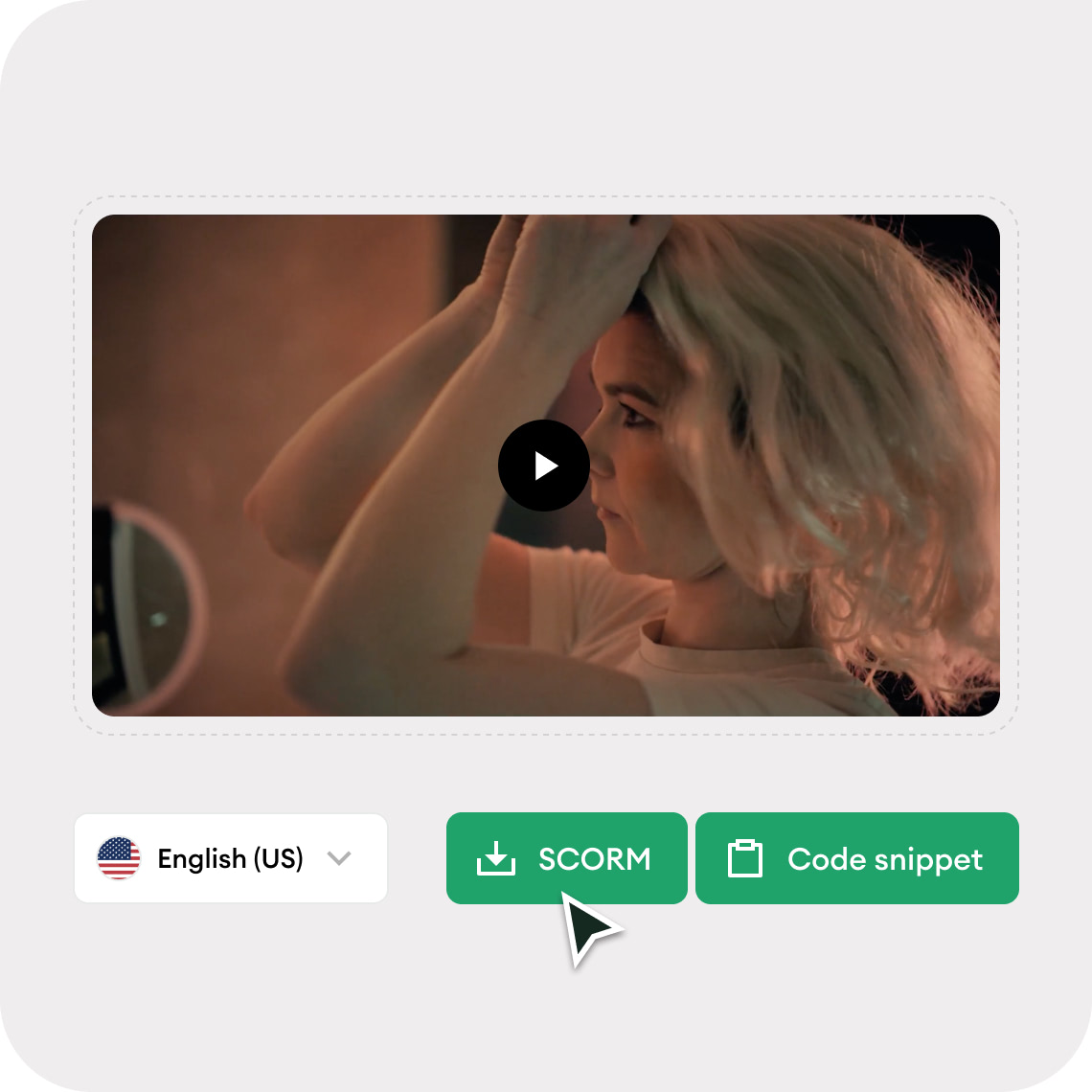
Train people in their native language
Our content is localized with voice-overs by professional actors and native speakers. It’s accessible with captions and available in 18+ languages
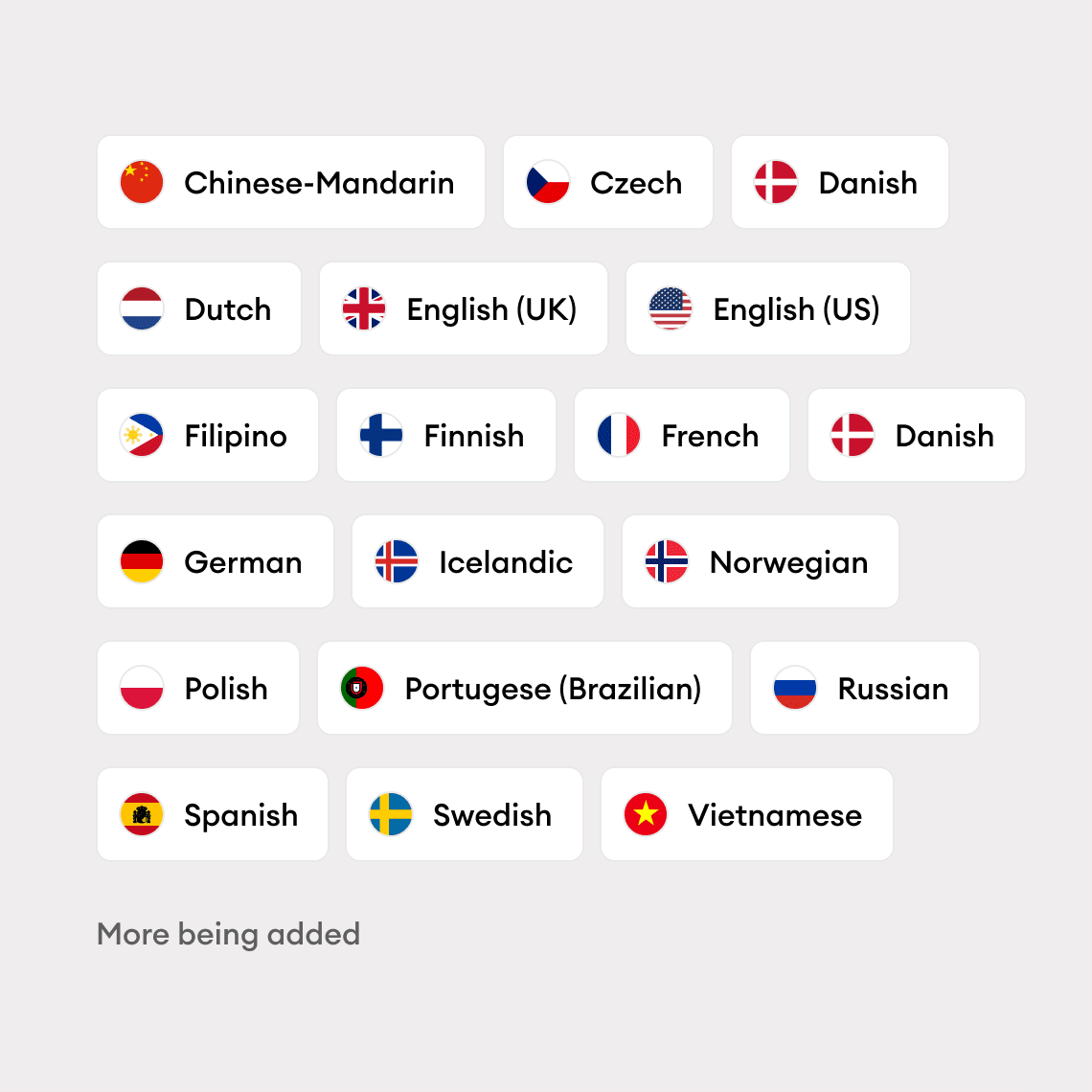
Cover the full spectrum of cybersecurity awareness
Short story-driven videos that don’t bore or hurt productivity
Each video has a quiz to reinforce learning
Add company-specific instructions, links to relevant resources, etc.
Make cybersecurity top-of-mind in your physical spaces
Add your company branding, telops or short messaging
We release new videos regularly to cover emerging threats
Available in 18 languages with more being added
Two times 2022 Bronze Telly Award Winner
Explore how to deliver targeted training and how to track human cybersecurity resilience in your company
Measure employees’ cybersecurity knowledge and behavior before and after training
Achieve compliance and build security culture with curated behavior-changing training programs
You and your employees are going to love AwareGO. It’s a modern, cloud-based system for managing human risk, from assessment to remediation. We’ve made it super easy — schedule your first assessment or training in minutes.
Get started for free and give it a go right now.
You’ll love the way AwareGO can fit into your existing infrastructure. Our robust APIs, widgets, and content available in SCORM format make sure that the integration is seamless. We also integrate with Active Directory, Google Workspace, and popular tools like Slack and Teams.
Contact us and our experts will recommend the best way to integrate.
Upgrade your cybersecurity business by adding human risk management to your existing portfolio of services. Increase your deal size by leveraging Human Risk Assessment or offering Security Awareness Training to your current customers and creating a new revenue stream.
Contact us to become an AwareGO partner, and we will support you every step of the way.

Your 2024 security training program is already obsolete.You’re right to feel like you're constantly playing catch-up. AI-powered social engineering......

Your annual GDPR training is probably a waste of time.There, we said it. You push your team through dull modules, check a box for the auditors, and......

In 2023, the Verizon Data Breach Investigations Report confirmed a stark reality: 74% of all breaches involve the human element. Your technology...

The 2023 Verizon Data Breach Investigations Report confirmed a stark reality: 74% of all breaches involve the human element. That means for every...

74% of all data breaches involve the human element, according to Verizon's 2023 DBIR. Yet, how much of your security budget is spent on technology...

Your annual security awareness training is making you less secure. It’s a bold claim, but the data supports it. You invest in programs, employees......

Your annual security training is over. A week later, how much do your employees truly remember? The forgetting curve is a real threat, and those...

Is your security training budget working? It’s a tough question to answer when you can’t measure the return. You see insurance premiums rise and know....

In today’s enterprise landscape, cyber threats evolve faster than ever. Employees are the first line of defense and often the weakest link, and securi...

If you’re an MSP, MSSP, consultant, training provider, or LMS vendor, you’ve likely heard this from clients: “Our cybersecurity training is boring.” “...